The Need for Threat Mitigation

In order to minimize risks and potential harm, threat mitigation is vital to ensuring security for an organization.
Digital risks can damage an organization’s reputation and image. To have a successful digital risk protection plan, organizations must employ multiple mitigation strategies to proactively protect organizations from risks becoming significant threats.
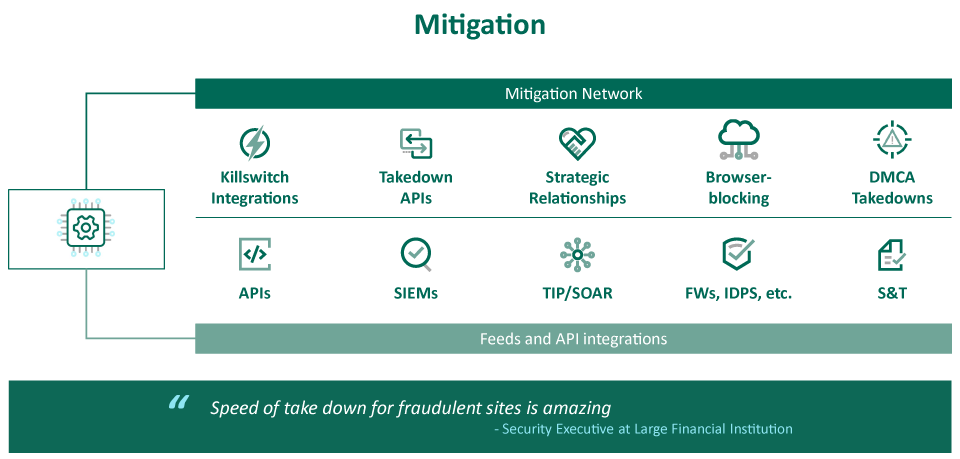
Fortra’s PhishLabs delivers a complete mitigation strategy through an extensive global takedown network built on years of trust with service providers along with browser-blocking, DMCA takedowns, and automated integrations with internal controls. Instead of relying primarily on manual entries, or automated form submissions and emails, the PhishLabs Platform connects directly to service providers via proprietary killswitches and takedown APIs. This delivers the fastest and most successful takedown capability in the industry. By combining takedown, browser-blocking, the ability to remove copyright infringed content and images, and integration with internal security controls, PhishLabs ensures threats are quickly and completely mitigated.
Protect your organization from external threats that risk your reputation and brand and ensure stronger digital risk protection. Make sure your organization has a comprehensive mitigation strategy.
Stop External Threats with a Global Takedown Network
To ensure the quickest external threat mitigation in the industry, PhishLabs utilizes an extensive range of takedown services. Partial mitigation strategies, such as integrating threat indicators into internal, frontline security controls, are not enough to prevent harm to brands, customers, and employees. PhishLabs delivers a complete mitigation.
Actionable Alerting and Reporting for Rapid Remediation

The PhishLabs Web App provides organizations complete visibility into their mitigated threats. This includes the following features.
- Threat Intelligence Indicators – As part of the curation process, PhishLabs’ expert analysts gather threat intelligence to find actionable intel.
- Incident Data Reporting – As part of PhishLabs’ mitigation, organizations receive reports with mitigation efforts, targeted brand activity, and threat actor patterns.
- Incident Creation – Threats are documented through an incident creation in the PhishLabs Web App. There, users can review incidents details, including statuses, threat types, sources, dates and timestamps, and mitigation start dates.
Benefits of Cyber Threat Mitigation
- Automated threat detection for comprehensive security
- Ability to immobilize threats at scale
- Protection and achievement of organizational goals
Address Threats Quickly and Completely
PhishLabs delivers the most comprehensive and effective mitigation in the industry. By combining takedown, browser-blocking, and integration with internal security controls, we ensure threats are quickly and completely mitigated - protecting an organization's brand, customers, and employees. Our mitigation efforts are not only threat-specific but also vary significantly depending on the infrastructure or platform where a threat resides.
The sophistication of our solution is well beyond sending emails and manually filling out abuse forms. We provide complete mitigation including fully automated killswitches. When a PhishLabs analyst identifies a threat, we have a direct integration into the relevant provider's infrastructure that automatically takes it down. Our established takedown APIs automatically positions mitigation requests to the front of provider’s internal ticketing or workflow systems and if infrastructures and platforms are unable to quickly support direct integration, PhishLabs' strategic relationships expedite our requests.
The high-fidelity nature of our curated threat data also makes it valuable for feed and API integration into internal security controls, such as SIEMs, TIPs, SOARs, and firewalls, highly enriching the frontline defense tools used to stop threats from reaching internal users, regardless of the incident’s current mitigation status.