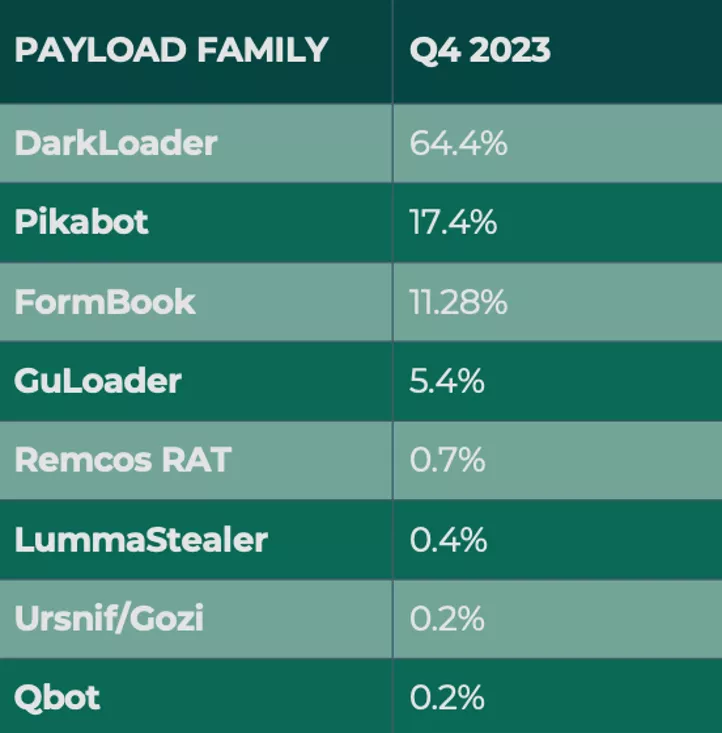
In Q4, three malware families represented more than 93% of all payload volume targeting end users, with Malware-as-a-Service (MaaS) DarkLoader leading all other reports. Fortra first received reports of DarkLoader in user inboxes in Q3, with attack volume picking up significantly beginning in October. The shift to criminal activity associated with DarkLoader comes after coordinated efforts by officials in Q3 to disrupt former malicious powerhouse QBot. Newcomer Pikabot and popular MaaS FormBook also helped fill the void left in QBot’s absence, with the majority of malware attacks linked to one of those three families.
Malware as a whole increased quarter over quarter, making up just under a percent of all email attacks targeting corporate enterprises. While minimal compared to credential theft or response-based threats, email payloads remain the primary delivery method of ransomware targeting organizations and can result in extensive monetary loss and reputational damage. In order to prevent malware from reaching user inboxes, Fortra continuously monitors payload families reported in corporate inboxes. Below are the top payload threats to enterprises in Q4.
DarkLoader
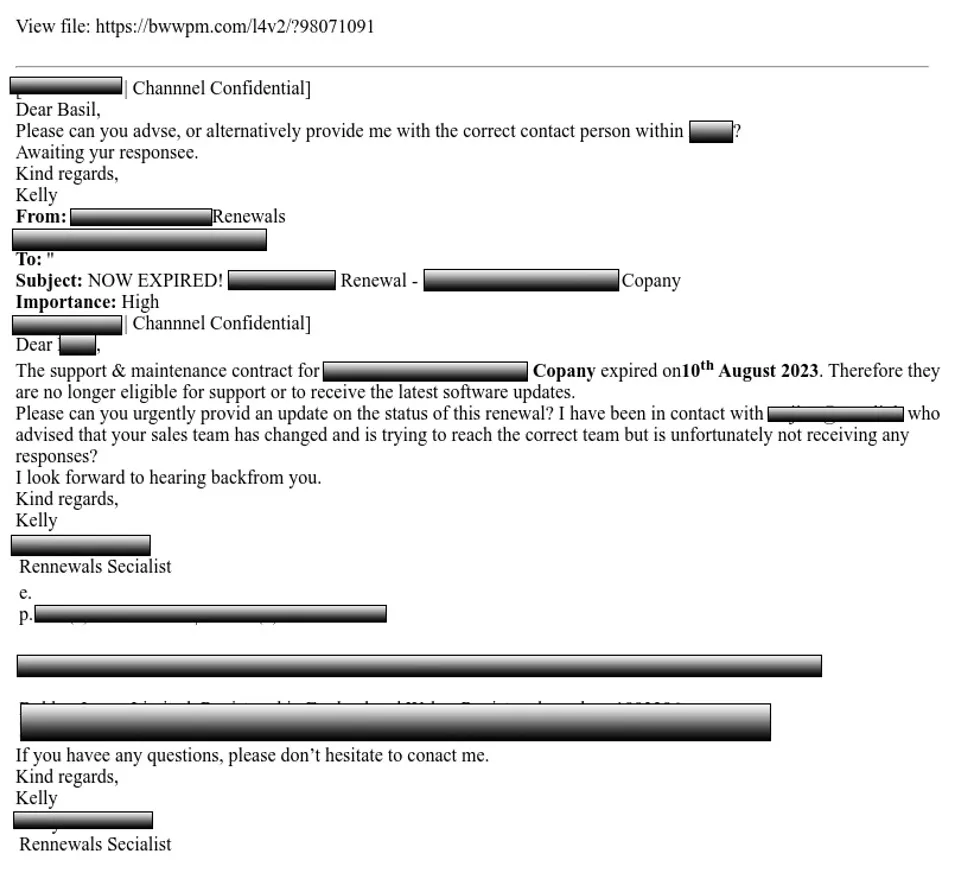
Remote access trojan DarkLoader made up nearly 65% of all payload reports in Q4. Available as a limited malware-as-a-service (MaaS), DarkLoader has been unattainable to many threat actors due to the cost associated with its pricey subscription model (up to 15k a month.) DarkLoader attacks are distributed in a variety of ways, including email phish and messages via compromised Microsoft Teams accounts.
DarkLoader capabilities include keylogging, credential theft, privilege escalation, and anti-analysis. Previous activity has been linked with ransomware group Black Basta.
Below is a DarkLoader phishing email. The payload was delivered via PDF attachment.

Pikabot
Developed in 2023, Pikabot was the second most reported payload in Q4 with 17.4% of total volume. Q4 2023 is the first time Pikabot has been reported to PhishLabs by end users. The malware is considered both an advanced backdoor and loader, with a variety of features including the ability to avoid sandboxes, run shell commands, and self-terminate if a system language is Georgian, Kazakh, Uzbak, Tajik, Russian, Ukrainian, Belarusian, or Slovenian.
Pikabot is frequently distributed via email thread jacking campaigns.
Below is a Pikabot phish distributed to the end user in an email thread campaign. The payload was delivered via a PDF attachment.
FormBook
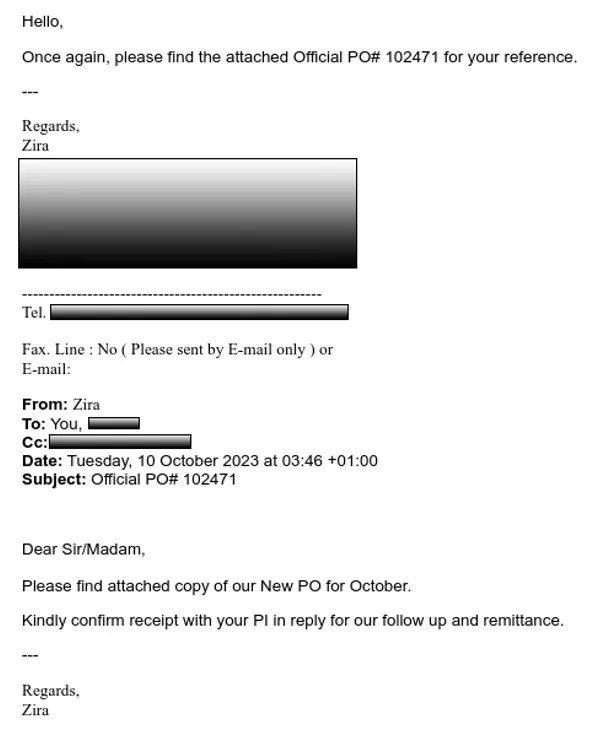
The FormBook payload family contributed to more than 11% of payloads in Q4. Accessible via MaaS, FormBook is considered an affordable malware due to its low advertised price on dark web marketplaces. It is also widely known as easy to implement for criminals with low technical acumen. FormBook typically infects devices via phishing emails delivering the payload through a variety of file type attachments.
FormBook is capable of receiving control commands that allow threat actors to manipulate infected devices. Malicious features include form-grabbing and key logging, with credential theft stealing capabilities and anti-evasion functions such as anti-debugging.
The below is an example of a phishing email delivering FormBook within a malicious .XLS file.
The payload landscape shifted in Q4 as threat actors moved to replace the void left in QBot’s absence. While DarkLoader has so far led all other malware families in volume, it remains to be seen whether it will continue to be the choice of attackers, especially when presented with other options viewed as more attainable. Given the novelty of Pikabot, a similar focus will be on its operational performance and whether or not criminal groups decide to make this newcomer their payload of choice in 2024.
Learn How Fortra Helps Protect Against Malware Attacks