Understanding how cyberattacks unfold is key to stopping them. In this blog, Fortra’s threat researchers break down the anatomy of a recent smishing campaign, revealing the tactics, techniques, and infrastructure behind the attack.
The Smishing Attack
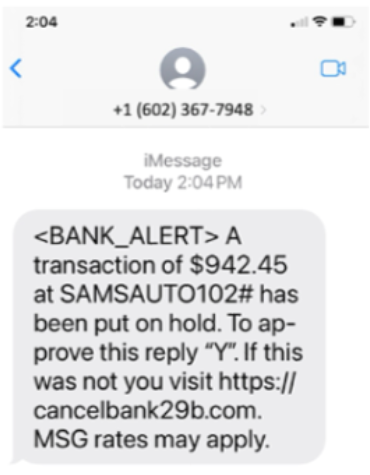
The smishing text contains a banking alert about a transaction being put on hold and urges the reader to visit the link if the transaction was not initiated by the recipient. Given that this is an unsolicited text message about an unknown transaction, combined with the urgent tone of the text, the user is likely to be tricked into clicking the phishing URL and visiting the malicious site.
SMS Sender Verification

Typically, a telltale sign of identifying a smishing attack is four-digit numbers because they indicate the use of email-to-text services. However, the attacker is using a standard complete number in this smishing campaign to bypass identification through this well-known detection technique.
Unlike email-based phishing, smishing attacks can't be reliably blocked by sender phone numbers, which are often recycled and reused by legitimate entities. Phone numbers also lack the telltale signs — like spelling or grammar errors — used to flag suspicious emails. These traits allow attackers to bypass security controls more easily and increase the likelihood their messages reach intended victims.
Landing Page Analysis
The following screenshots were anonymized to protect the privacy of Fortra’s clients.
Fortra identified a phishing kit that offers multiple variations of this landing page. These landing pages frequently impersonate well-known brands, including major banks, national retailers, and mail carriers.
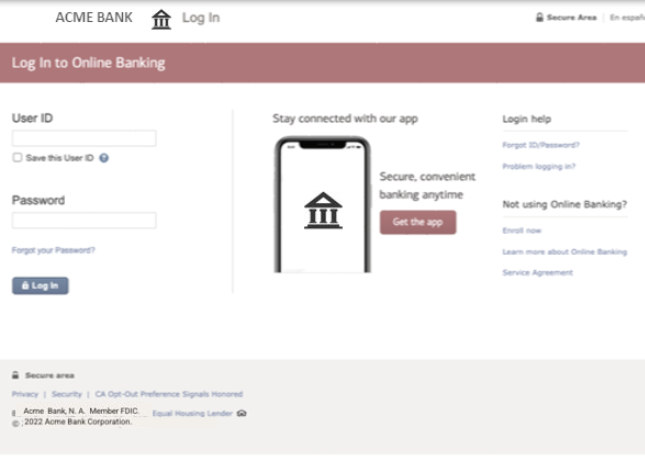
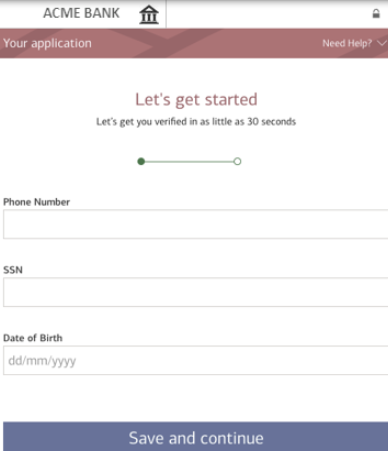
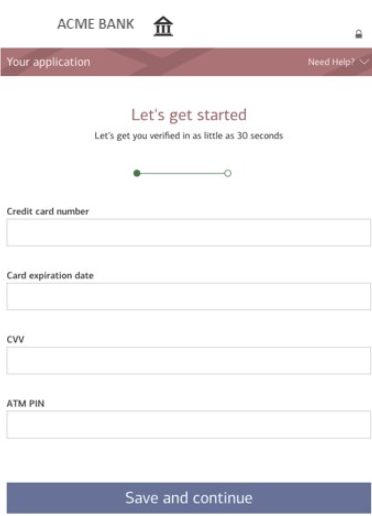
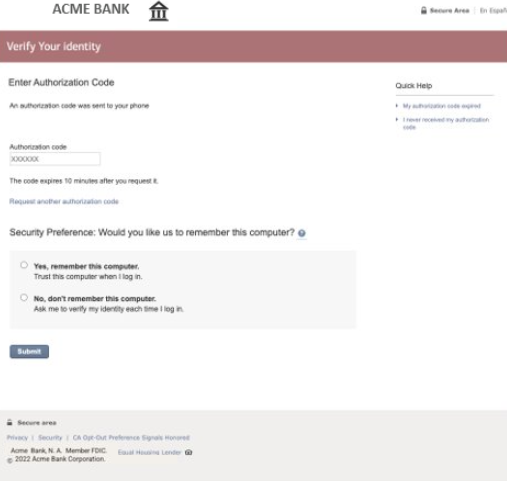
The initial landing page asks the user to enter their banking login information, luring them into compromising their credentials by providing them to the attacker. Upon clicking on the “Log In” button, the user is taken through a couple of pages that prompt them to provide sensitive personally identifiable information (PII) such as their social security number (SSN) and credit card number. Victims are tricked into revealing sensitive information, putting them at risk of identity theft, credit card fraud, and other malicious activity. Exposed personal data can also be weaponized to create highly targeted spear phishing attacks.
The attack chain ends with the adversary luring the victim into giving up their multi-factor authentication (MFA) code. The inclusion of a security preference question at the bottom of the page reinforces the site’s legitimacy and gives users a false sense of security. Attackers then exploit the submitted MFA code and banking credentials to gain unauthorized access and carry out malicious transactions.
Suspicious URL Analysis
The smishing URL: https[:]//cancelbank29b[.]com
Unlike the landing page, the URL does not impersonate a specific brand or identity because the domain name refers to a generic “cancelbank.” The vague domain name, combined with a random string like “29b,” can signal a suspicious URL and prompt users to question its legitimacy.
Fortra conducted a WHOIS lookup query on the smishing URL which revealed ingenuine information.
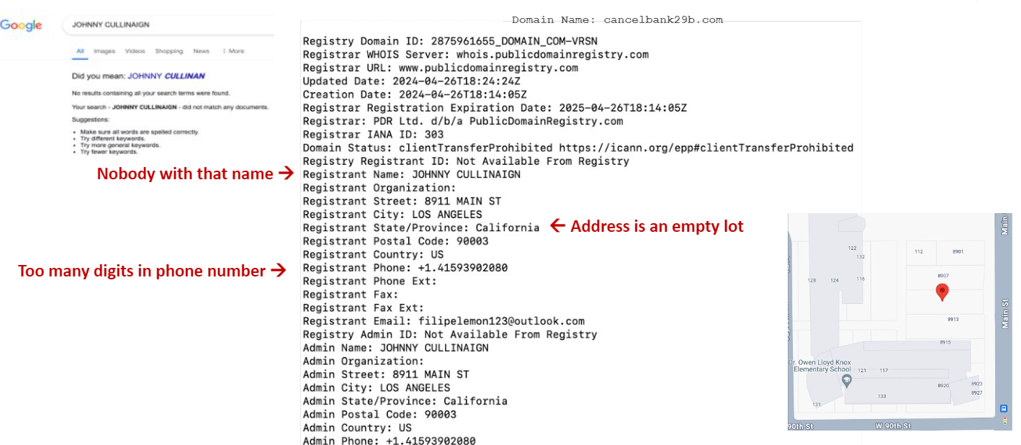
A quick Google search demonstrated the registrant’s name does not exist, and the registrant’s address is an empty parking lot. Additionally, the registrant’s phone number contains too many digits. These bogus details raise doubts about the legitimacy of the registrant, further alluding to the malicious motivations of the threat actor.
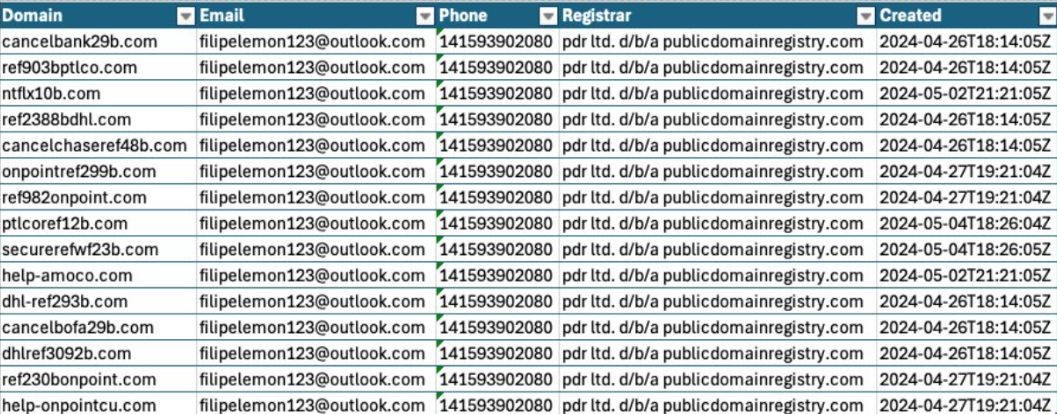
However, the query exposed the registrant’s email address, which Fortra used in a reverse WHOIS lookup to uncover additional domains potentially linked to the attacker:
Strengthen Your Defenses Against Social Engineering with Smarter Cybersecurity Training
Social engineering attacks are no longer limited to the familiar phishing email. They’ve evolved into highly sophisticated and varied threats, including smishing campaigns that exploit users through text messages. This growing diversity in attack methods makes it increasingly difficult for users to recognize and respond to cyber threats. That’s why robust security awareness and training programs are essential to building strong cyber defenses.
Fortra Brand Protection and Fortra Human Risk Management solutions empower organizations to cultivate a resilient cybersecurity culture, equipping users to stay vigilant and respond effectively to the ever-changing threat landscape.