Business Email Compromise attacks are some of the most costly and vicious forms of phishing. Unlike the standard pray and spray approaches to phishing, they take a great deal of research and personalization to persuade a victim to hand over their credentials or wire them funds. This week we're taking a closer look at how invoice scams work, just one of the many sub-types of BEC or spearphishing attacks.
Phishing is defined as social engineering using digital methods for malicious purposes. And just like any other phishing attack, a threat actor will use social engineering in an effort to breach a network or receive company funds.
One way they do this is through sending a fake invoice, either from a vendor they are known to work with, a made-up vendor, or from a trusted brand.
How Invoice Scams Work
Invoice Scams typically work in one of two ways: through fake invoices with a goal of receiving money or by prompting a victim to put their credentials into a fake login screen.
The latter of the two is a bit more simple and follows the typical phishing lure approach.
- Threat actors conduct research on target
- Threat actor spoofs an email address of the victim's CEO or executive
- Threat actor uses research to craft targeted message, develop urgency
- Victim see's email from executive or CEO
- Victim clicks a link to review an invoice (this can be anything from reimbursement to a large annual SaaS tool)
- Victim inputs their private information into phishing site
- Threat actor breaches network
In some cases, the attack can be further propagated now that they have a real email address, and in other cases, they may be able to access the necessary information they were going after. And then there is the more complicated invoice scam that sets its sights on money.
- Threat actors conduct research on target (usually someone with financial controls)
- Threat actor spoofs an email address of victim's CEO, executive, real vendor, or fake vendor
- Threat actor uses research to craft targeted message, develop urgency
- Victim see's email with an invoice attached, which is normal for their role
- Victim follows standard protocol of paying out on the invoice
- Victim wires funds over to the threat actor
- An eventual audit takes place and the company realizes how much money is lost
In both situations, the company will be at a financial loss, but if a threat actor gains entry into the network, they can cause far more damage and even fly under the radar more easily.
This year's IC3, an annual report released by the FBI, shows just how costly and impactful these threats are.
“In 2018, the IC3 received 20,373 BEC/E-mail Account Compromise (EAC) complaints with adjusted losses of over $1.2 billion. BEC/EAC is a sophisticated scam targeting both businesses and individuals performing wire transfer payments. The scam is frequently carried out when a subject compromises legitimate business e-mail accounts through social engineering or computer intrusion techniques to conduct unauthorized transfers of funds."
According to this year's Phishing Trends and Intelligence report, among the most targeted industries are cloud storage brands (12.6%), email providers (24.1%), payment services (11.1%), and SaaS products (7.2%). This doesn't mean that threat actors are targeting the employees of the brands (though that is also the case), but more so the users of them. For example, Dropbox or Adobe products may be used in a phishing lure, just as an Office 365 logo may be added to another.
Take for example this warning notice from the FTC last year that vaguely mentions a brand being impersonated, sending out a fake invoice tied to their service, and then promptly stealing the victim's credentials when being prompted to login.
The IC3 report goes on to detail some of the components involved in these BEC attacks:
"BEC and EAC are constantly evolving as scammers become more sophisticated. Through the years, the scam has seen personal emails compromised, vendor emails compromised, spoofed lawyer email accounts, requests for W-2 information, and the targeting of the real estate sector."
Even internally here at PhishLabs, we too saw one of the more popular scams that attempted to spoof a companies CEO. An email that appeared to be sent from our CEO was sent to numerous members of our team, had a simple opening line without a link, and prompted the victim to have a text-based message on their phone. The goal? Gift cards. Nobody in the company fell for it; however, given the prevalence of the attack, it's likely other's have.
Invoice Scams in the Wild
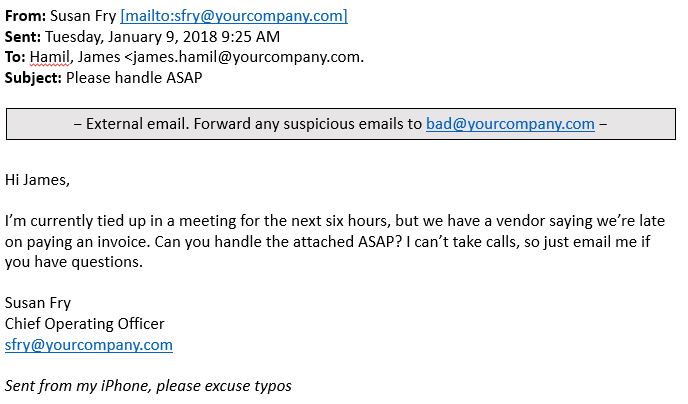
The following are just a few of the reported invoice scams that have made a real-world impact.
Tech Targets: By impersonating Quanta Computer, a vendor that both Google and Facebook use, a threat actor from Lithuania nabbed $123 million.
“The scheme also involved fake invoices, contracts, and letters that increased the chances of targeted employees agreeing to send money to the specified accounts." a Security Week report stated.
Inside Job: An employee on the accounting team for Kia abused her role and knowledge of processes to embezzle nearly $1 million in funds by issuing fake invoices.
Scamming the Church: Would you pay to use some of the features on social media? That is what one particular threat actor tried to do and targeted Zion Lutheran Church in Texas. It wasn't very effective.
Yellow Pages Scam: Remember when people relied on Yellow Book for listings and businesses had to pay a lot to advertise there? Those days are gone, but the scams still float around. A Wisconsin-based Farmer's Insurance was targeted by such as scam and a fake invoice, but this time was supposedly from a collections agency looking for just under $500.