Fortra has identified active phishing campaigns capable of evading email security gateways and filters. This analysis outlines key tactics, real-world examples, and related threat indicators.
Sample Email Lure
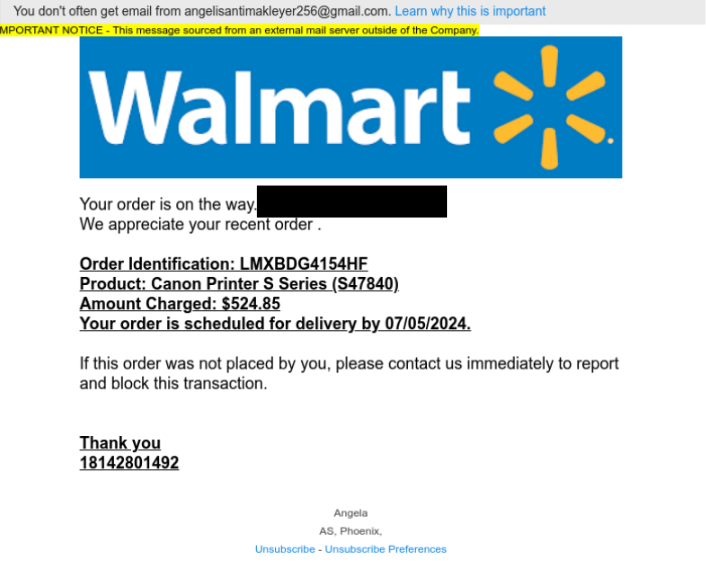
Sample 1: Vishing Example
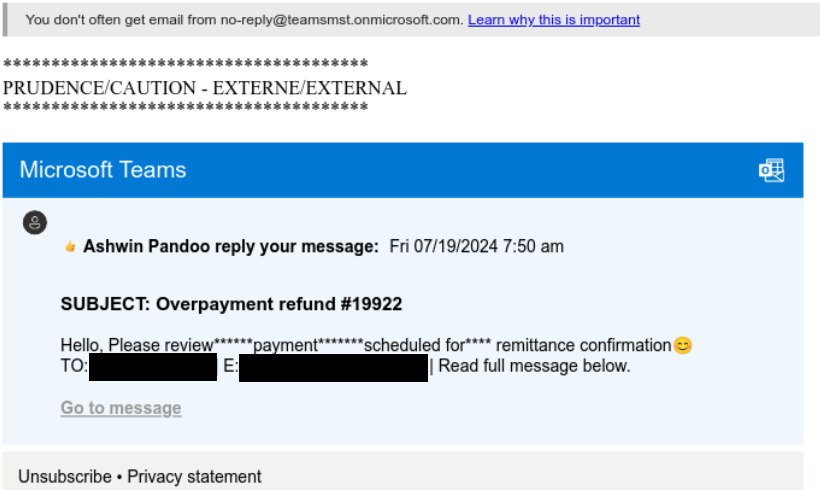
Sample 2: Office365 Phishing Example
Sender Verification
Analysis: Fortra identified a trend of Twilio SendGrid being used for phishing and vishing email campaigns. These emails pose as different senders, with notable examples that include popular brands and large organizations such as Walmart, Apple, Target, Microsoft, and PayPal.
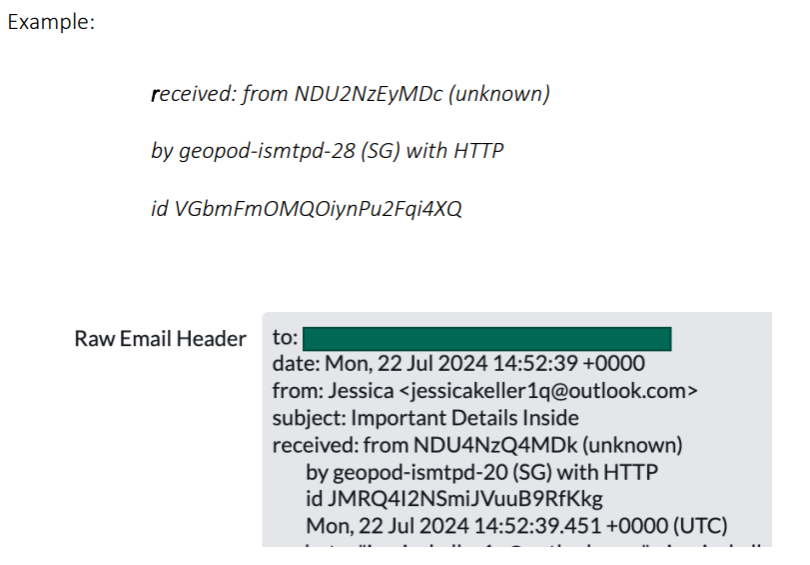
While there is no fixed sender email that can be consistently used as an indicator, as the sender’s email and name often vary with each malicious email, Fortra identified the following commonalities and patterns which can facilitate the identification of these emails. The first commonality is the received field in these phishing emails is usually classified as “unknown.” Each time an email jumps from one SMPT server to another, a new “Received: ” header is added to the message. However, these emails typically contain a “Received: from (unknown)” which means that there was no reverse DNS information provided from the last server that the email came through. The received field also commonly contains “geopod-ismtpd,” which has been classified by SendGrid abuse reports as being associated with phishing, spam, and spoofing.
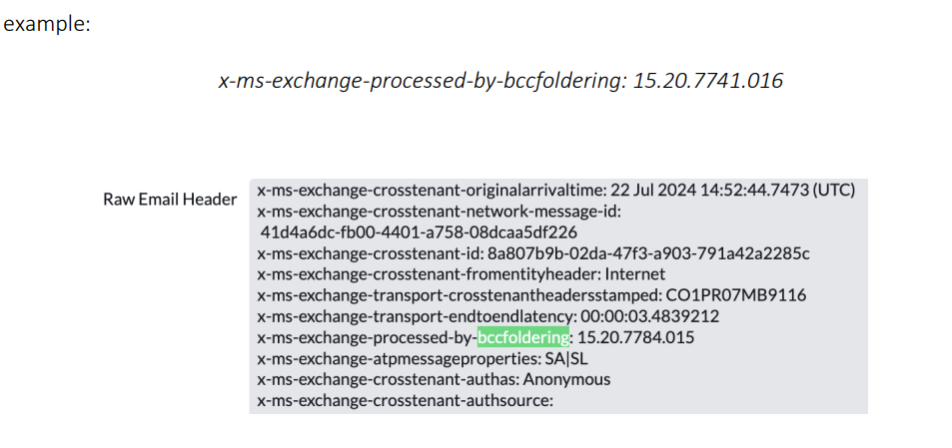
The next identified pattern is the use of bccfoldering as the primary method for sending these phishing emails rather than the cc field. Unlike the cc field, which displays the recipients, bccfoldering hides the recipients by adding them only to the email envelope, not the headers. This makes the recipients undetectable unless the server is configured to reveal them. The adversary uses this tactic to conceal the scale of the phishing campaign, as concealed recipients can make it difficult to detect how large the phishing campaign is.
Finally, there is a notable discrepancy between the sender’s email and the brand typically being spoofed. For instance, in the first lure example that impersonates Walmart, the sender’s email is angelisantimakleyer256@gmail[.]com which is a personal Gmail account that is not affiliated with Walmart. This discrepancy can alert the user of suspicious emails.
Email Content Analysis
Analysis: While the email content varies based on the brand impersonated, these emails all commonly claim the recipient made a purchase and must dispute the charges by calling a provided number or clicking a link. The mention of disputing a financial charge can create a sense of panic in the user, which attackers exploit to illicit a quick response. By posing as large and well-known organizations, in combination with these urgent financial warnings, attackers increase the likelihood that the recipient will interact with the link or phone number out of fear. The attacker also poses as different organizations in order to impact as many users as possible.
URL Inspection
Analysis: Although the URLs differ with each attempted phishing attack, Fortra identified the following commonalities in these phishing links. When a phishing link is provided instead of a vishing phone number, the adversary utilizes SendGrid’s link tracking feature which causes the phishing link to be associated with the SendGrid platform. This tactic allows the attacker to leverage the genuine reputation of the SendGrid platform, as the URL will be SendGrid affiliated which hides the malicious link. The URL typically directs the user to a fake Microsoft Office365 login page, where the user is further lured into compromising their login credentials. Fortra has observed that the captured personal identifiable information (PII) from these campaigns can often be found for sale on account marketplaces or forums on the deep/dark web. The PII will either be posted for sale as individual accounts depending on how valuable it is, or it will be posted for free as a credential dump file for other threat actors to exploit.
Threat Indicators
Unavailable due to the varying and dynamic nature of this attack campaign.
Learn more about how to protect your organization from digital threats with Fortra Brand Protection.