Active phishing campaigns are coordinated attacks that Fortra has observed bypassing email security gateways and filtering tools. The following analysis includes examples, high-level details, and associated threat indicators.
Sample Email Lure
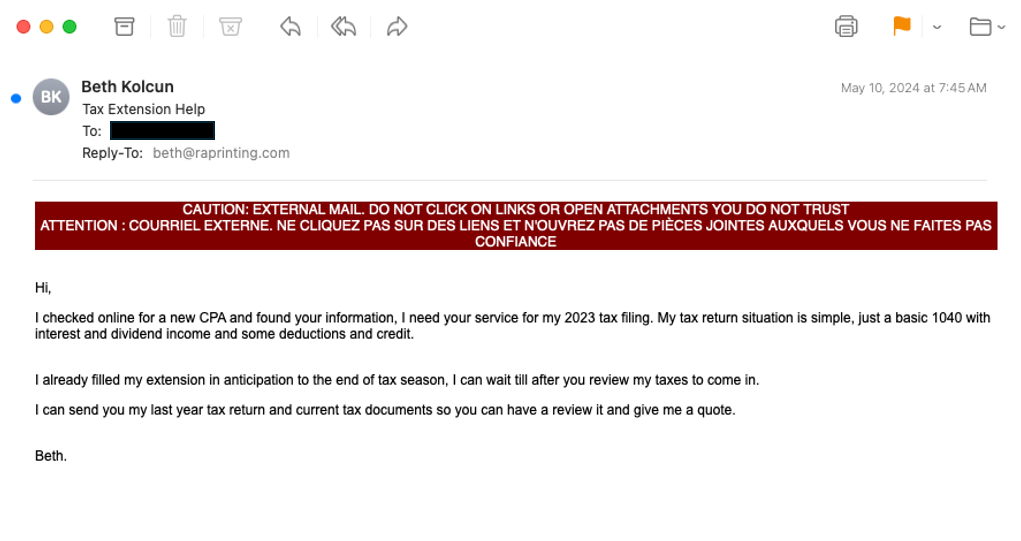
Sender Verification
- Sender’s Email: ogawa@kidscorp[.]jp
- Sender’s Name: Beth Kolcun
- Reply-To Address: beth@raprinting[.]com
- Analysis: The email seems to be from a legitimate source. However, there is a clear mismatch between the sender’s email address and the reply-to address. This tactic is often used by threat actors to redirect email responses to an email address under their control, suggesting that the attacker is attempting to conceal their identity under the “kidscorp.jp” domain.
Email Content Analysis

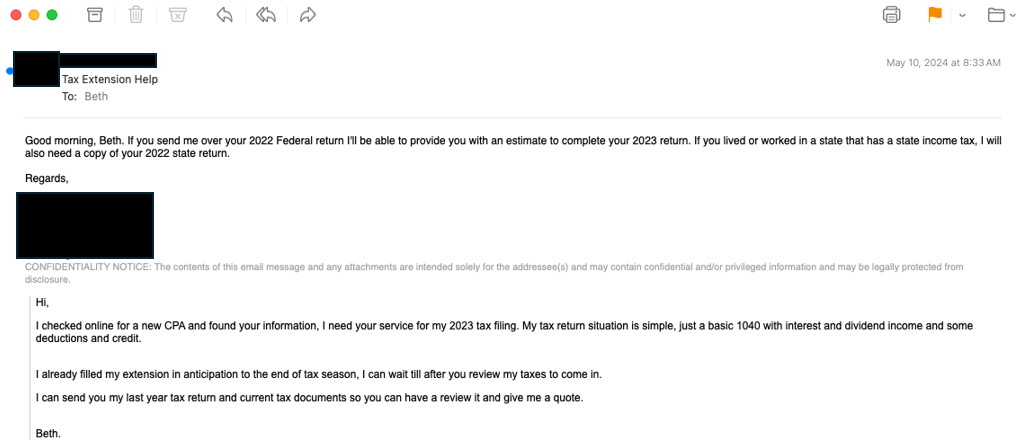
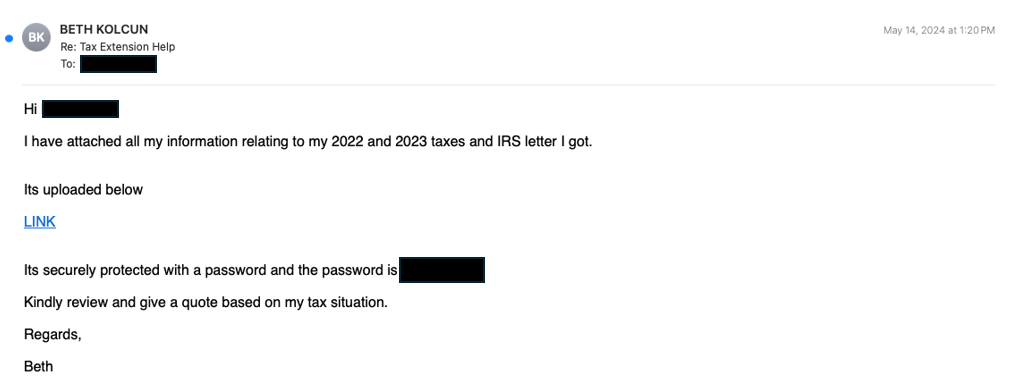
Analysis: The email contains a request for assistance with tax filing. Upon engaging with the sender to provide additional information, the recipient receives a URL to download a password protected file. The attacker’s usage of a password-protected file creates a false sense of security that may further deceive the user into clicking the link and downloading the file. Additionally, by uploading the file and sharing a link rather than including it directly within the email, the file can avoid immediate scanning by email filters which is a tactic the attacker uses to conceal malicious files from detection.
URL Inspection
URL: The “LINK” leads to hxxps://acrobat.adobe.com/id/urn:aaid:sc:VA6C2:3926ed3f-f846-4dde-903c-0ae658308645
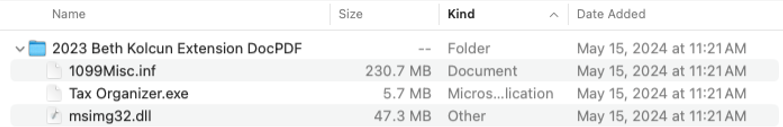
Analysis: The destination URL leads to a legitimate Adobe Acrobat page where a password-protected zip file is shared for download. Using Adobe Acrobat to distribute the attachment increases the likelihood that the user will click on the URL due to the credibility of the file sharing platform being used. Additionally, password protecting a zipped file allows the attacker to evade anti-virus scanners because the file cannot be unzipped without the password. Hence, most anti-virus scanners are unable to unpack or scan the contents of the attachment which allows the attacker to further bypass security measures. Entering the password unzips the attachment into three files, the most notable of which is the executable “Tax organizer.exe”. This executable is not identified as malicious by anti-virus scanners, which can mislead the user into assuming the entire attachment is safe. This false sense of security can lead them to click on other files, such as the DLL file “msimg32.dll” which contains the widespread Remcos RAT malware.
Threat Indicators
- Sender's Name: Beth Kolcun
- Sender's Email: ogawa@kidscorp[.]jp
- Alternate Sender's Email: sheltereu@shetlerprinting[.]com
- Reply-To Address: beth@raprinting[.]com
- Email Subject: Tax Extension Help
- Alternate Email Subject: My Estimates Payment Is Ready Now for Filing
- DLL File SHA256 Hash: 6d7d32231705522b3e2c302da6e662a64f05f52b09b311c6577c9076fef11e11