Historically, the average brand is targeted by 40 look-alike domains per month. Look-alikes are a strategic component of malicious lures and websites and used in a variety of spaces including social platforms, text messages, the open web, and email. An attack that incorporates a look-alike domain can mean the difference between a convincing campaign and a suspicious one, with a versatility that allows them to mislead victims and their security tools.
In our Brand Threats Masterclass, experts discussed the tactics threat actors use to create look-alike domains and what organizations should do to protect against these threats. Below, we review the top ways threat actors will leverage look-alike domains in cyberattacks as we enter 2024.
Identifying Look-Alike Domains
Domains are spoofed in countless ways, with the brand, location, and industry of the target all capable of being incorporated into the URL. This makes identification of suspicious content an arduous task that requires comprehensive knowledge of where it can be found and how it can be abused to target your brand.
A well-crafted look-alike is easy to create and can appear legitimate even to a trained expert. Non-traditional spaces such as social media platforms and SMS have become hotspots for fraudulent activity, with look-alike domains functioning as a key component of manipulation. Look-alikes are most frequently incorporated into posts, advertisements, and text messages in these environments, acting as the vessel to phishing or counterfeit websites. Threat actors are also buying ad space on the open web that use a combination of look-alike domains and stolen branding.
Common Areas Where Look-Alike Domains are used:
- Social Media Accounts and Ads
- Credential Theft Phishing Sites
- Counterfeit Sites
- Search Engine Ads
- Phishing Emails
- SMS Attacks
Look-Alike Domain Tactics
In 2024, criminals will use a variety of techniques to build convincing look-alike domains. During Fortra’s Brand Threats Masterclass, Ryan Newby, Fortra’s Senior Security Operations Manager of Domain Services, recognized that the key to leveraging domains in an impersonation attack will start with the syntax of the URL.
“Threat actors will attempt to impersonate a brand by using direct or indirect hits on the brand’s title, the brand’s syntax itself, and the way it’s spelled. A lot of times this includes pairings with industry-related terms to make the URL syntax appear more convincing.”
Newby continued, “Common terms threat actors' pair with brands in the finance industry, for example, will include ‘finance’, ‘invest’, ‘portfolio’, or ‘stock.’ An attack targeting retail might have look-alikes with terms such as ‘store’, ‘sale’, or ‘clearance.’”
Second-Level Domain Manipulation
There are countless ways a look-alike domain can be constructed that will vary from the legitimate brand and appear genuine. In 2024, threat actors will primarily focus on the second-level domain to manipulate victims, knowing that it is purposefully selected by organizations to represent their brand. When registering a look-alike, threat actors will choose vocabulary that is similar to the legitimate domain or will slightly alter the existing name.
Below are common techniques threat actors use to create look-alike domains.
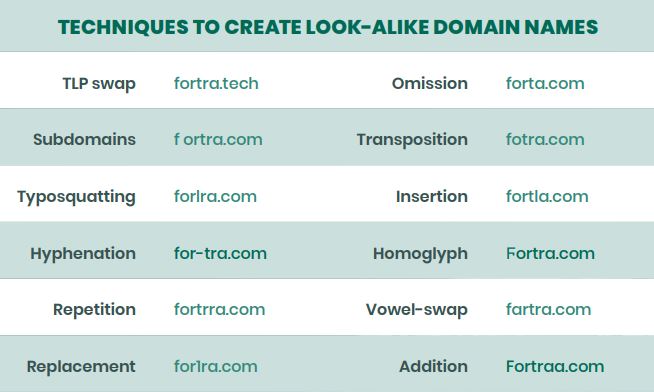
Top-Level Domain Abuse
Last year, there was a stark increase in TLDs using terms clearly capable of misleading users in tech and retail. The TLDs that demonstrated the greatest growth in abuse were .info, .app, and .shop. Top-level domains will continue to see extensive abuse in 2024, with actors increasingly choosing to customize the TLD to the target industry.
TLD .zip was one of eight new TLD options rolled out to the public by Google in May 2023. .zip attacks quickly became a popular choice for threat actors and are expected to persist in the new year. The risks associated with a .zip TLD include downloading malicious files such as malware. Fortra’s Ryan Newby emphasized the challenges of .zip used in attacks.
“Unknowingly, you might be interacting with a malicious domain registration that is paired with a social media comment,” comments Newby. “If this domain points you to a .zip, then suddenly you’re downloading a file. That file could be malware that’s now blasted on your organization’s network or device.”
SSL Certificates
Looking forward, cybercriminals will also prey on the false sense of safety associated with SSL certificates. SSL certs have been a desirable component of look-alike domain attacks because they can be acquired at no cost and are very successful at conveying trust. Ryan Newby stressed the need to rethink associating SSL certification with authorized brands. “A lot of the time people think that an SSL certificate means that it’s safe to interact with them,” he explained. “All SSL is saying though, is that the person who registered the website, for example, is in fact the owner of the site.”
URL Shorteners
Tactics that manipulate look-alike domains further, such as URL shorteners, will also persist in the new year. While URL shorteners can be used to execute a scam in any space, they are especially popular for text or social media-based threats. Communication on mobile devices and social platforms occurs at an accelerated pace compared to email, and users are less likely to pause and confirm the legitimacy of the browser destination before clicking on a link.
Protecting Your Brand
A combination of employee education and broad monitoring of the threat ecosystem will be critical to protecting against look-alike domains this year. Due to the lack of awareness that many employees have around cyber threats on non-traditional spaces such as social media and mobile, training should include basic security concepts such as analyzing URLs before clicking on them and confirming that you are at the correct destination once you have followed a link. Employees should also have an easy way of reporting suspicious domains.
In order for organizations to adequately monitor for suspicious activity targeting their brands, security teams need broad visibility into new and existing domain registrations. This will aid in blocking malicious domains from entering the corporate ecosystem. This can be accomplished by analyzing registrations for brand-related keywords and variations to brand names. Additional intelligence should be collected from:
- TLD zone files
- SSL certificate transparency logs
- DNS traffic
